MikroTik RouterOS 7 回流問題解決方案
| 前言: |
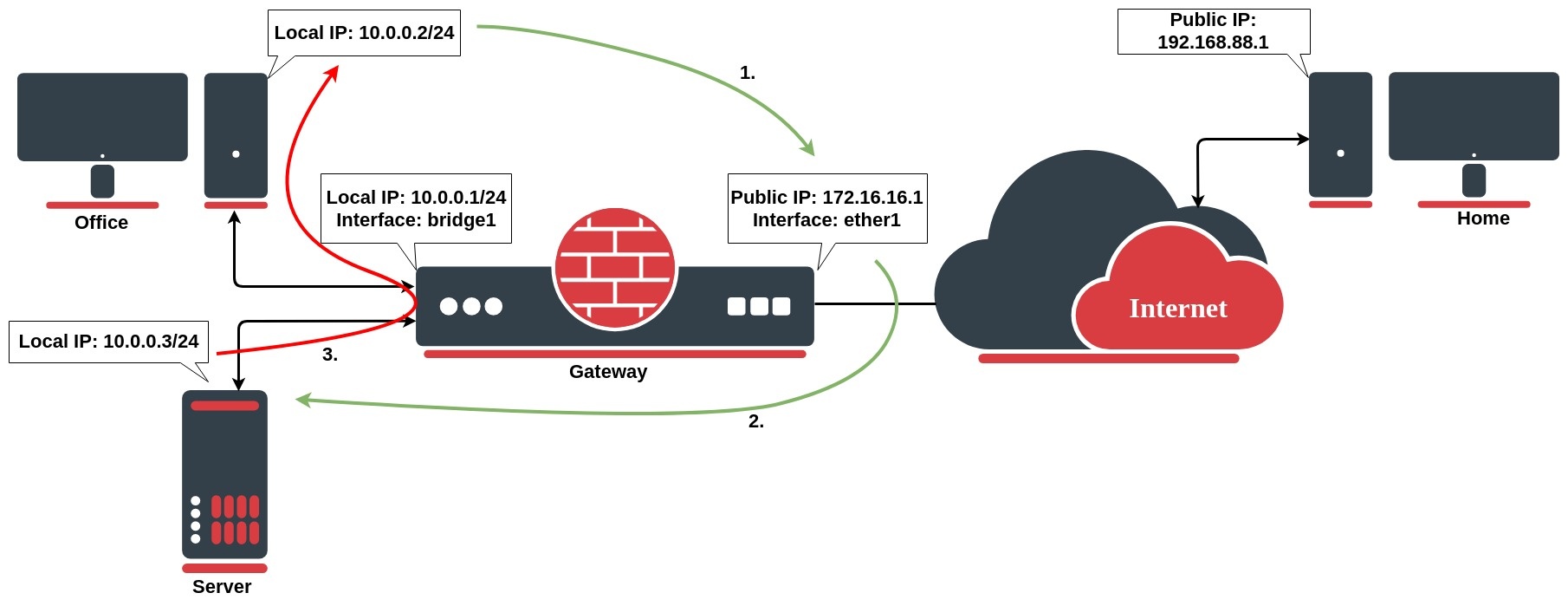
官方Hairpin NAT是指NAT Loopback即我們所說的回流,意思是LAN(同一內網)的裝置透過Public IP地址訪問LAN內的另一部伺服器,而沒有得到回應的問題。
| 如何產生回流-範例: |
LAN內網裝置A(10.1.1.10)想透過Public IP(221.112.252.254)訪問LAN內網的WEB伺服器B(10.1.1.99)。- 當
WEB伺服器B回應裝置A時,因為是同一網段10.1.1.0/24,所以WEB伺服器B不會經路由器(MikroTik Router)的Public IP作回應,而是直接回覆內網裝置A(10.1.1.10)使用10.1.1.99作為源地址。- 內網
裝置A(10.1.1.10)收到封包是WEB伺服器B(10.1.1.99),而不是原Public IP(221.112.252.254)的封包,最終會被丟棄。
| 解決方案: |
| 處理流程: |
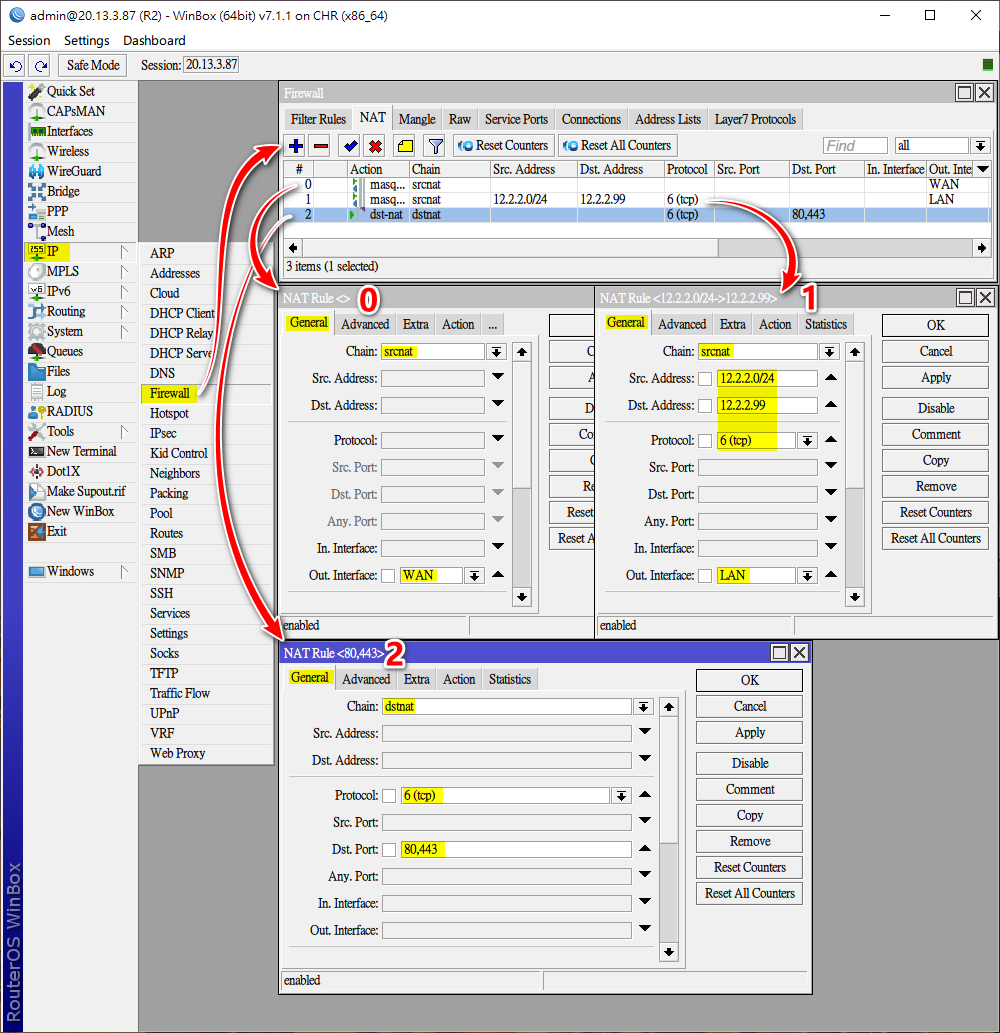
| 利用官方 Hairpin NAT 的解決方案 |
| 內網段 | 伺服器IP | 端口 |
|---|---|---|
| 12.2.2.0/24 | 12.2.2.99 | 80,443 |
Terminal 設定
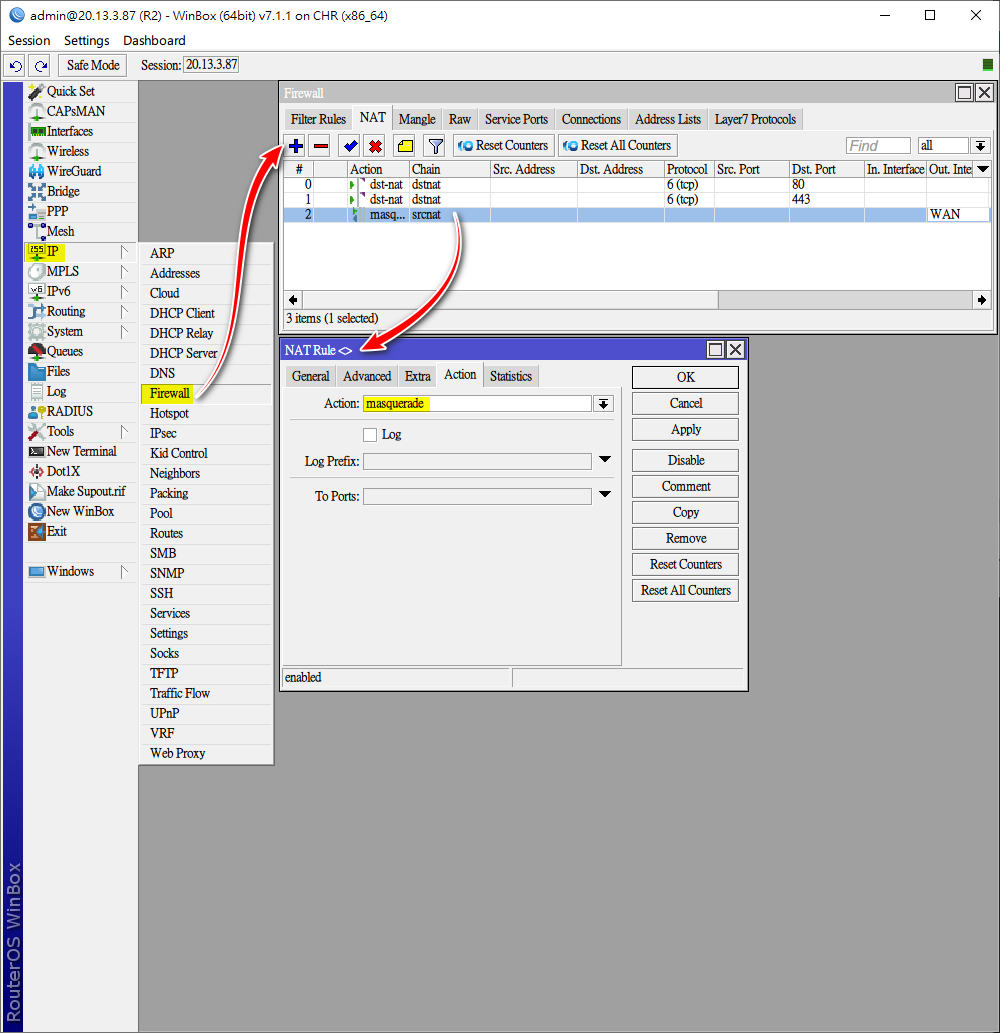
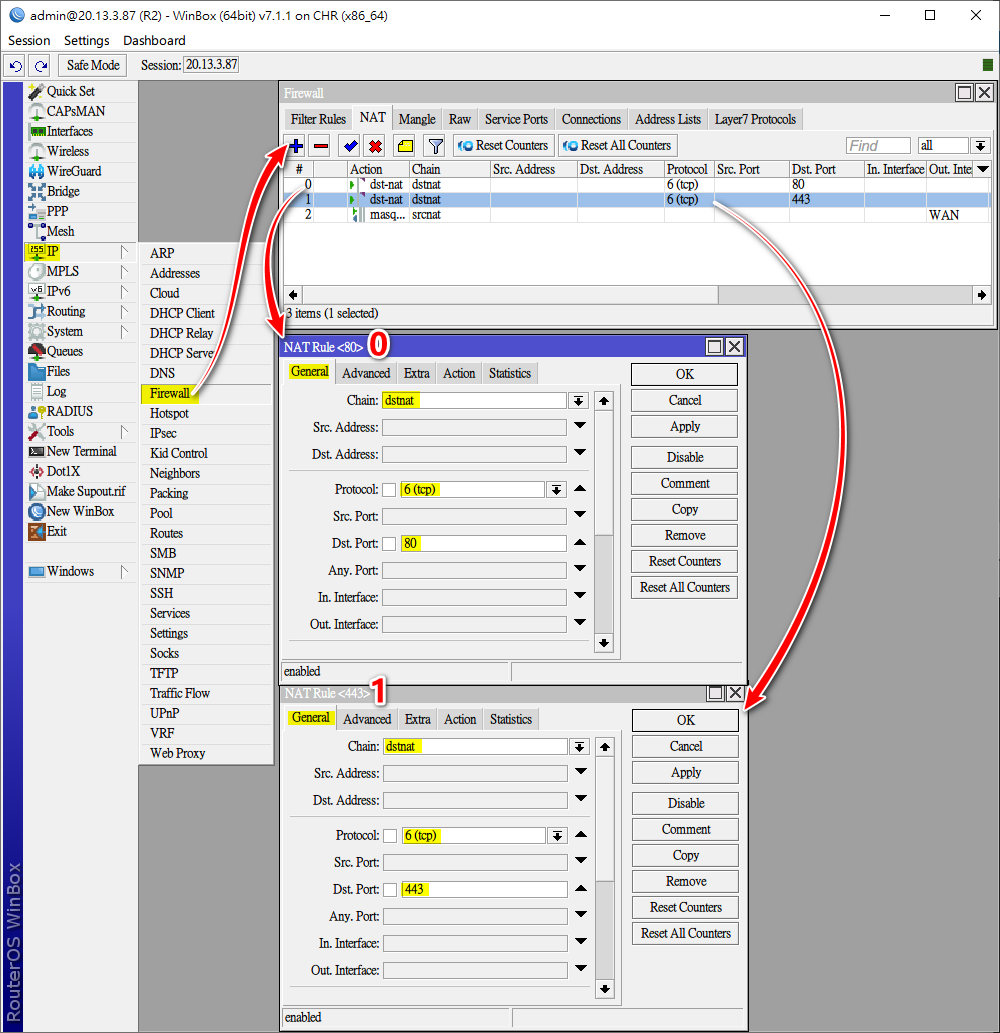
端口轉發(Port Forwarding) rules
/ip firewall nat
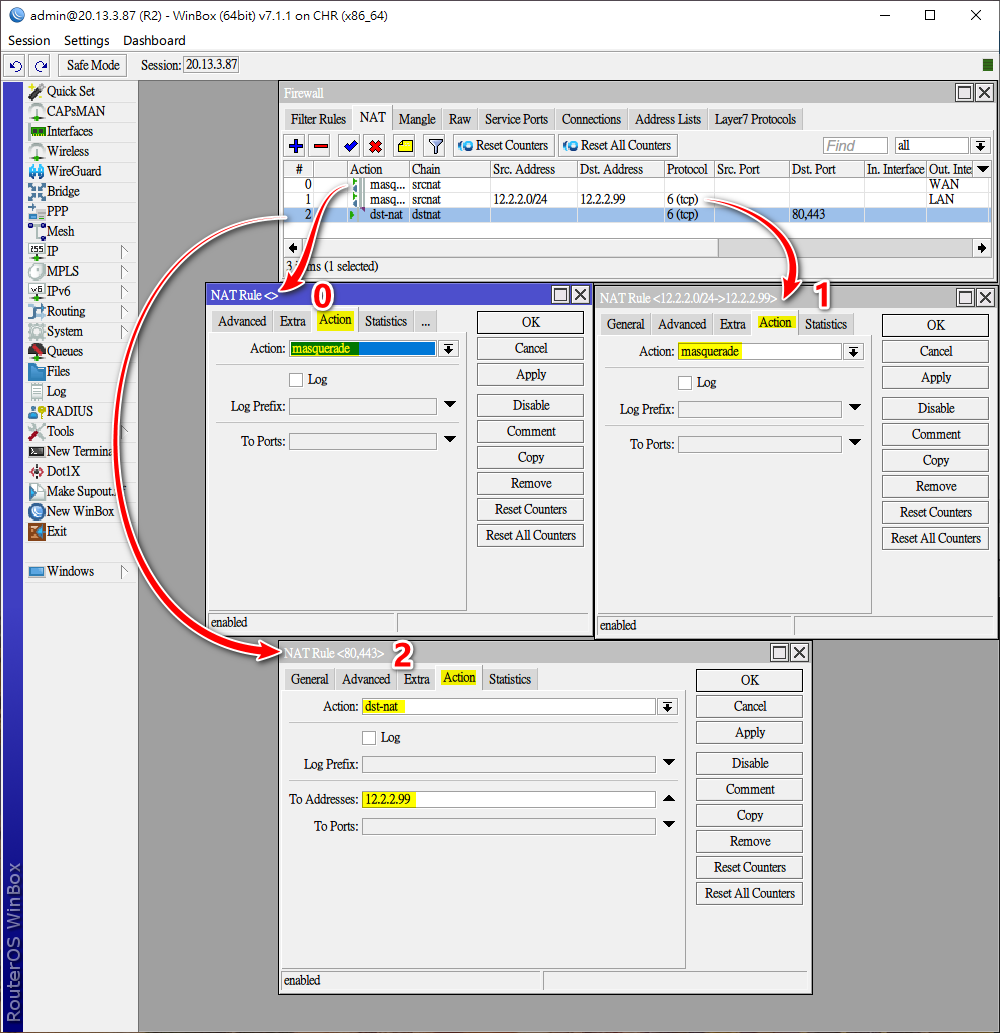
add action=masquerade chain=srcnat out-interface=WAN
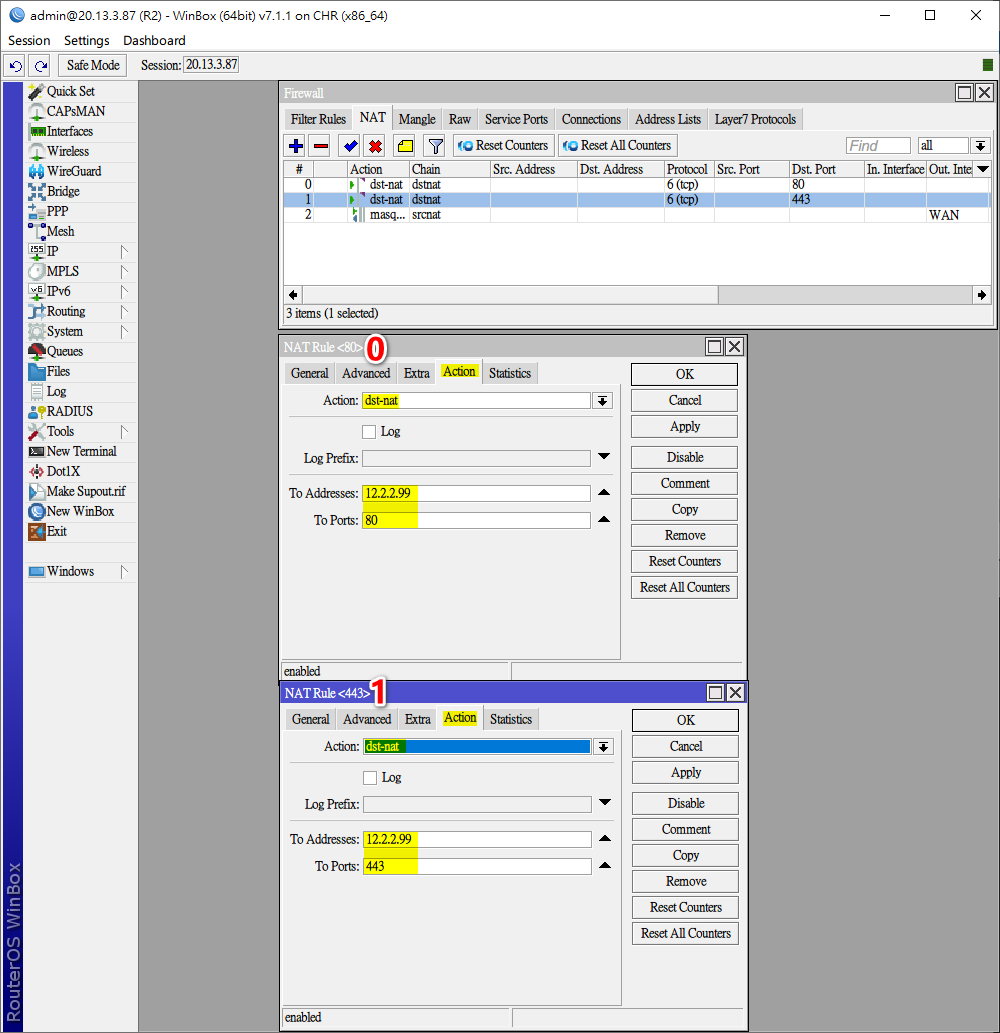
add action=dst-nat chain=dstnat dst-port=80,443 protocol=tcp to-addresses=12.2.2.99解決方法,新增src-nat rule
ip firewall nat add action=masquerade chain=srcnat out-interface=LAN protocol=tcp src-address=12.2.2.0/24[[返回目錄內容]]
| 利用DDNS功能的解決方案 (更多應用於動態的Public IP) |
如果是官方購買的路由器可以到IP>Cloud啟用DDNS功能,也可以用購買的域名做DNS A記錄。
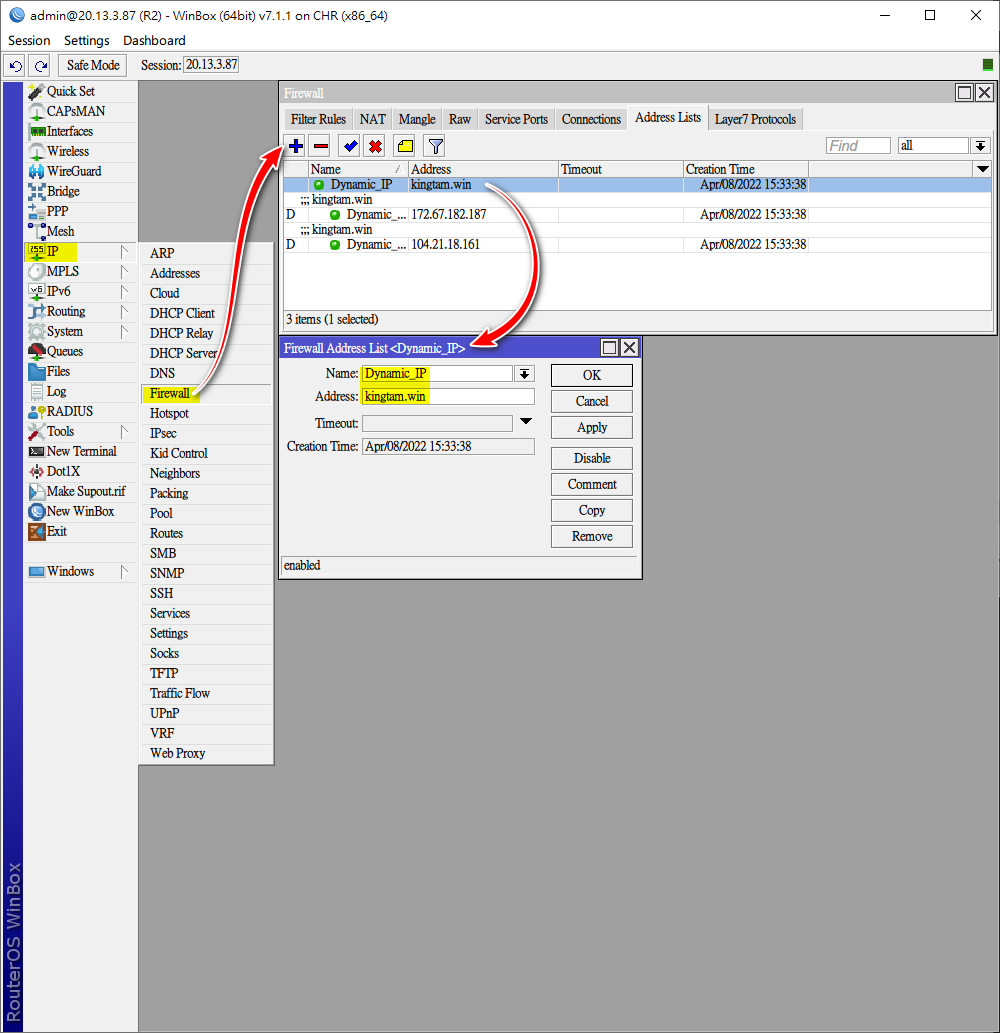
在IP > Firewall > Address Lists > 新增 + (官方的DDNS網址或購買的域名)
Name: 為Dynamic_IP(可隨意)
Address: 購買的域名地址
啟用動態流量偽裝
建立端口轉發(Port Forwarding) rules
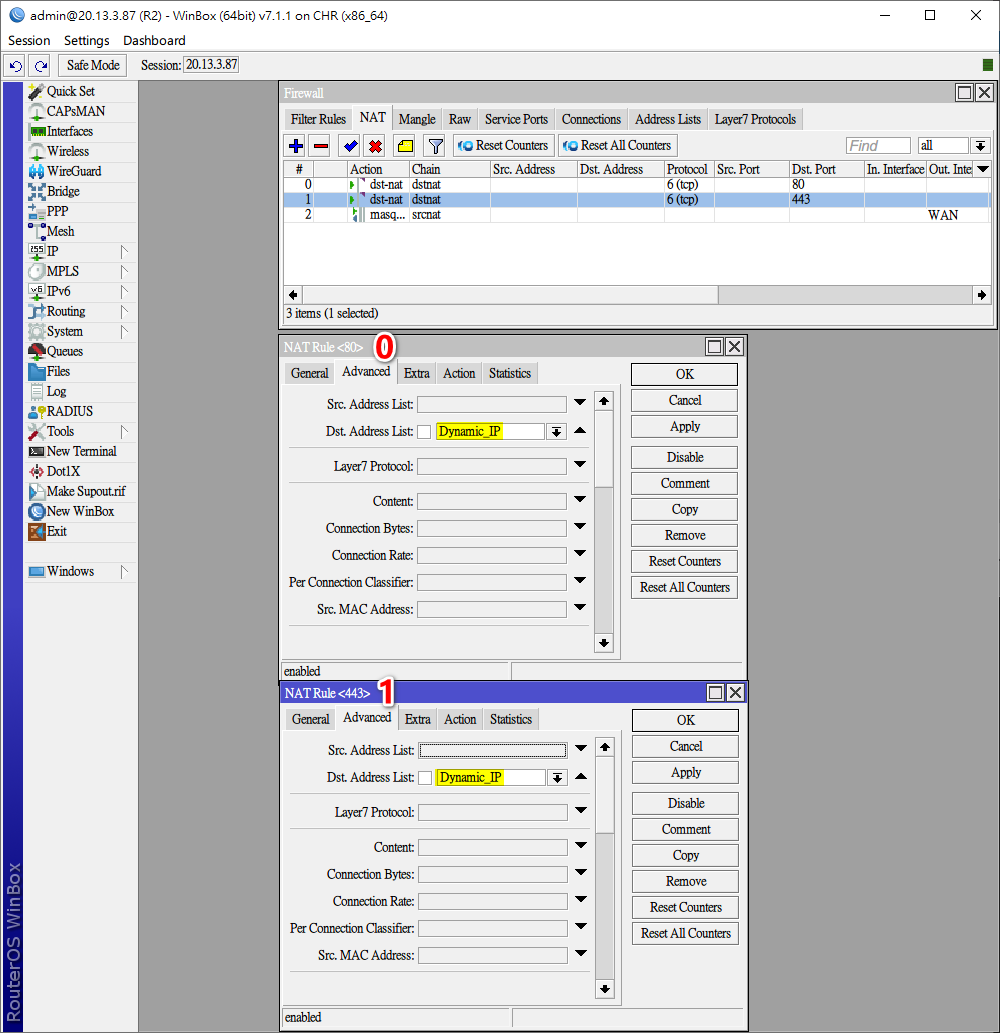
解決方法: Advanced > Dst.Address List: 選取剛建立的Address Lists 名稱為Dynamic_IP
Terminal 設定
啟用動態流量偽裝
/ip firewall nat
add action=masquerade chain=srcnat解決方法:
利用DDNS建立Address Lists
/ip firewall address-list
add address=kingtam.win list=Dynamic_IP修改原有的端口轉發(Port Forwarding) rules內的Address Lists
/ip firewall nat
add action=dst-nat chain=dstnat dst-address-list=Dynamic_IP dst-port=80 protocol=tcp to-addresses=12.2.2.99 to-ports=80
add action=dst-nat chain=dstnat dst-address-list=Dynamic_IP dst-port=443 protocol=tcp to-addresses=12.2.2.99 to-ports=443[[返回目錄內容]]
| 利用 Jump 命令的解決方案 |
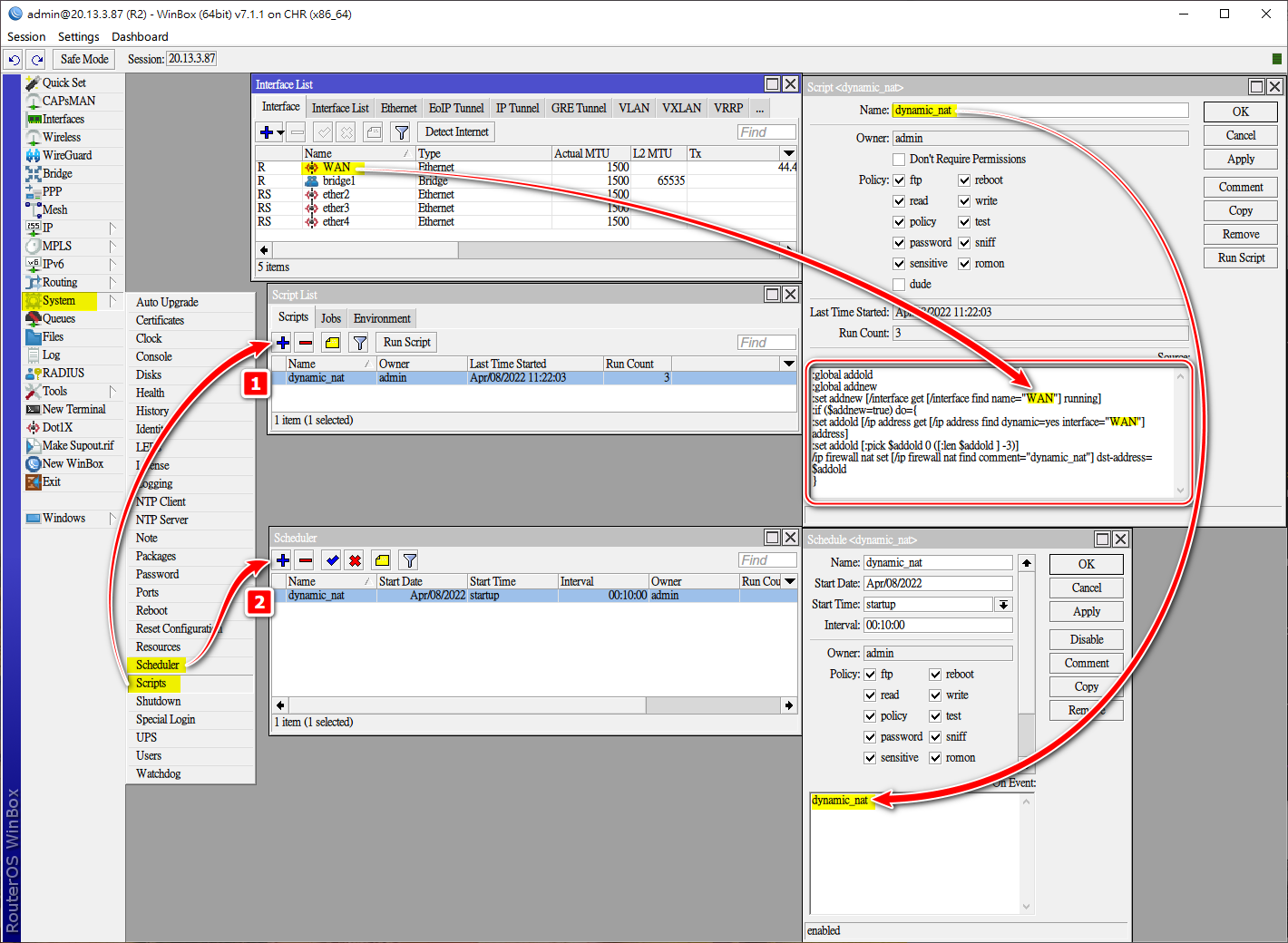
建立腳本(script)及排程(Scheduler),用於更新動態的Public IP
腳本(script)內容
:global addold
:global addnew
:set addnew [/interface get [/interface find name="WAN"] running]
:if ($addnew=true) do={
:set addold [/ip address get [/ip address find dynamic=yes interface="WAN"] address]
:set addold [:pick $addold 0 ([:len $addold ] -3)]
/ip firewall nat set [/ip firewall nat find comment="dynamic_nat"] dst-address=$addold
}| 變量 | 註解 |
|---|---|
| addold | 更新前IP變量 |
| addnew | 更新後IP變量 |
| WAN | 為Public網口WAN的名稱 (*根據路由器網口名稱變更) |
| dynamic_nat | 在nat表內查找comment(註釋)為"dynamic_nat"的rule, 更新其dst-address為現在使用的IP Address |
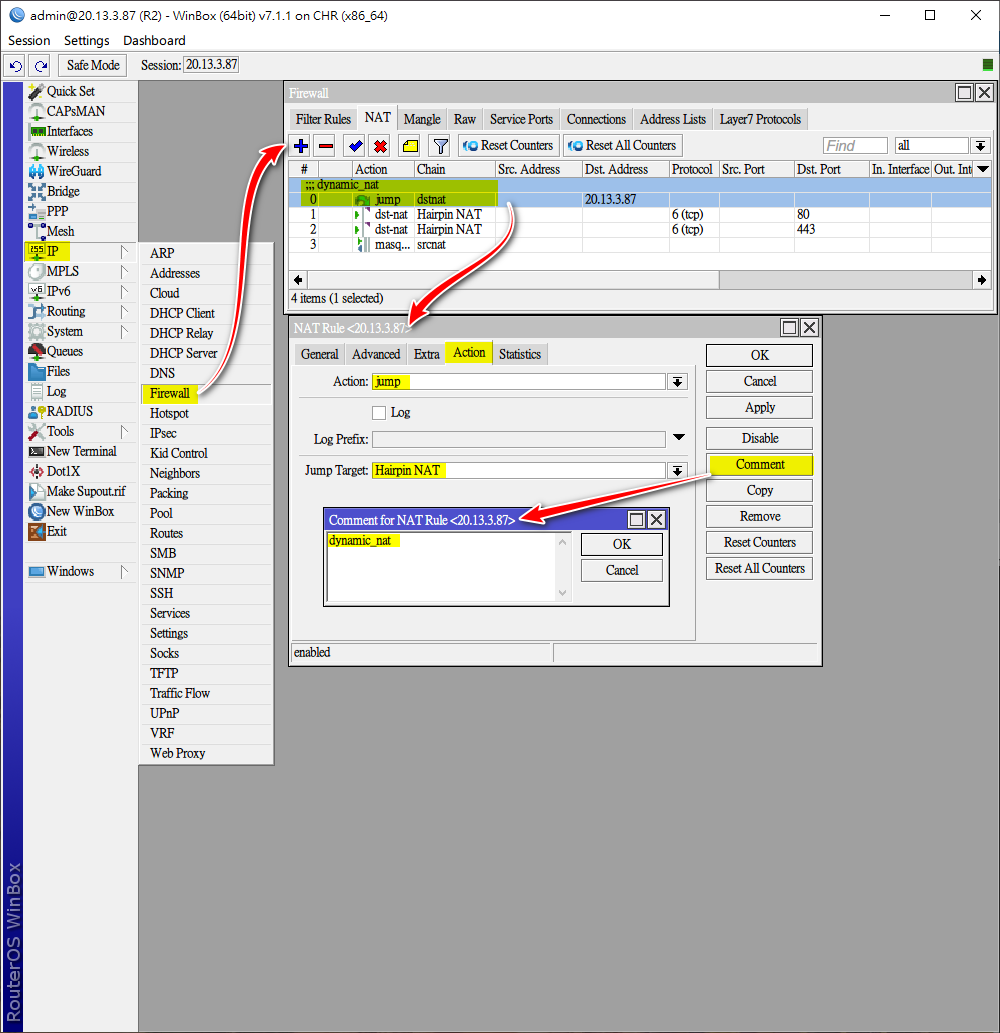
在NAT表建立jump rule,Jump Target: Hairpin_NAT
需要添加Comment(註釋)為dynamic_nat,因為上一步新增的腳本是根據Comment來更新rule內的Dst.Address
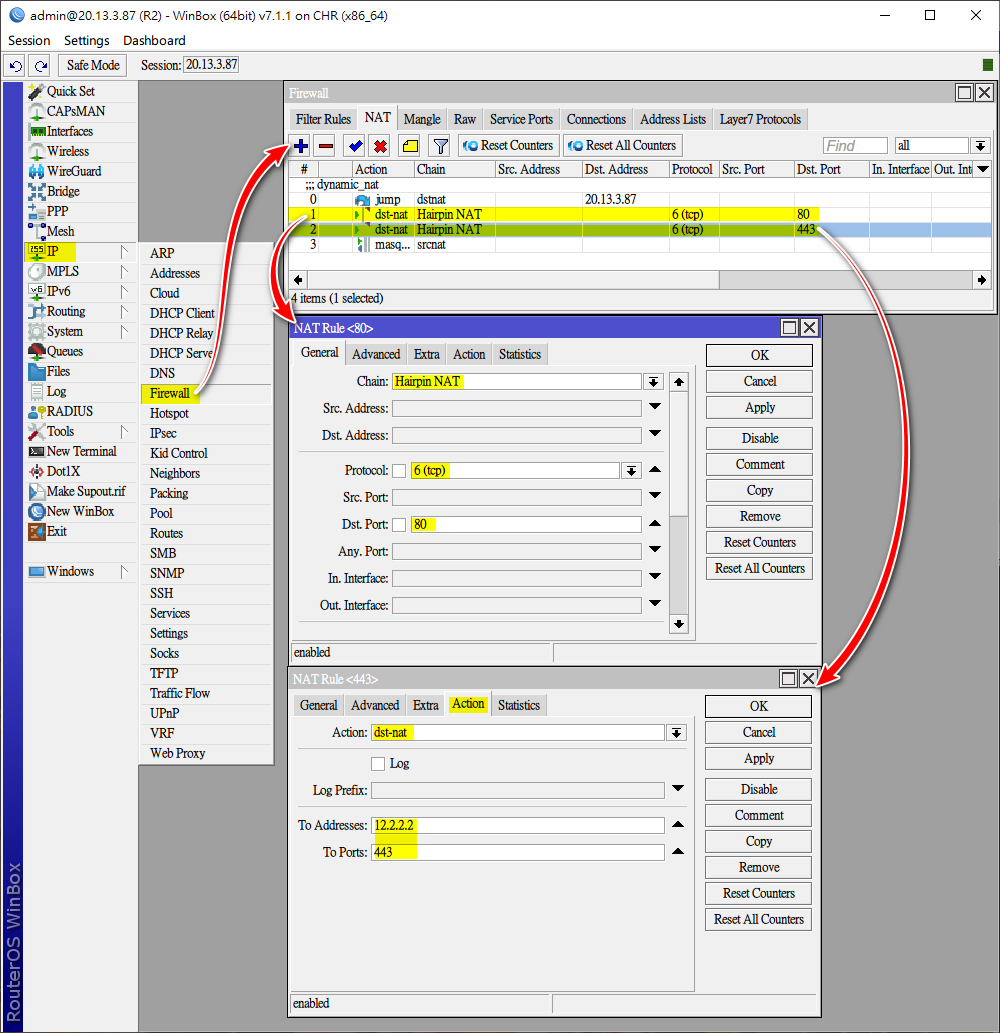
最後添加端口轉發(Port Forwarding) rules,其中Chain為Hairpin_NAT
Terminal 設定
建立腳本(script),用於更新動態的Public IP
/system script
add dont-require-permissions=no name=dynamic_nat owner=admin policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source=":global addold\r\
\n:global addnew\r\
\n:set addnew [/interface get [/interface find name=\"WAN\"] running]\r\
\n:if (\$addnew=true) do={\r\
\n:set addold [/ip address get [/ip address find dynamic=yes interface=\"WAN\"] address]\r\
\n:set addold [:pick \$addold 0 ([:len \$addold ] -3)]\r\
\n/ip firewall nat set [/ip firewall nat find comment=\"dynamic_nat\"] dst-address=\$addold\r\
\n}"建立排程(Scheduler)
/system scheduler
add interval=10m name=dynamic_nat on-event=dynamic_nat policy= ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon start-time=startup在NAT表建立jump rule,Jump Target: Hairpin_NAT
/ip firewall nat
add action=jump chain=dstnat comment=dynamic_nat dst-address=20.13.3.87 jump-target="Hairpin NAT"最後添加端口轉發(Port Forwarding) rules,其中Chain為Hairpin_NAT
/ip firewall nat
add action=dst-nat chain="Hairpin NAT" dst-port=80 protocol=tcp to-addresses=12.2.2.2 to-ports=80
add action=dst-nat chain="Hairpin NAT" dst-port=443 protocol=tcp to-addresses=12.2.2.2 to-ports=443
add action=masquerade chain=srcnat[[返回目錄內容]]
| 結語: |
三種解決方案可根據自身情況進行選擇及設定,最為簡單是使用路由器自帶的DDNS功能域名地址解決,也可以透過DNS的Static功能處理回流問題。
| 參考資料: |
其实最核心的部分就是動態流量偽裝
是的. 國內封常用端口80,443. 可以要用其他PORT替換, 但現在家用有Public IPv4也不容易.